Executive Summary
Connected medical devices are becoming an essential part of modern healthcare. They enable more efficient processes and better treatment outcomes, but their growing complexity also introduces new vulnerabilities. Ensuring confidentiality, integrity, and resilience is therefore a central challenge for manufacturers and healthcare providers alike.
This report outlines:
- The key security requirements for medical connected devices
- Ongoing trends in the field of connected devices security
- Regulatory and technical developments
- Practical insights based on tools and solutions used at Vector Medical Engineering
The objective is to give a clear picture of the current connected devices security landscape without promoting specific products.
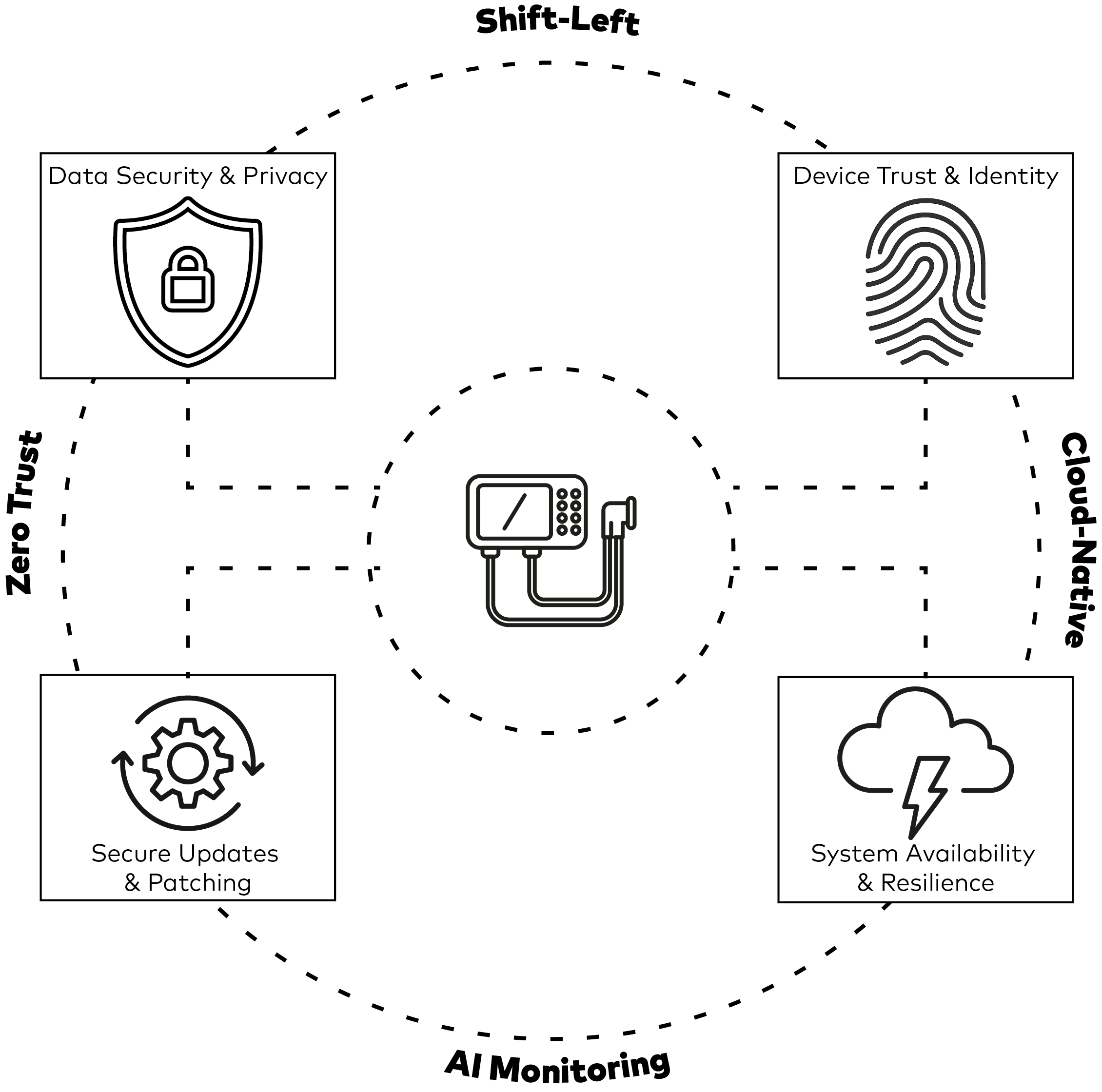
Security Needs in Connected Medical Devices
Data Confidentiality and Privacy
Medical connected devices collect and transmit sensitive health data. Protecting this data from unauthorized access is essential. Encryption, access control mechanisms, and compliance with privacy regulations like GDPR and HIPAA are necessary.
Device Identity and Trust
To avoid manipulation or impersonation, devices must have unique, secure identities. Features such as secure boot, signed firmware, and authentication certificates help ensure device trustworthiness.
Update Management
Devices need to receive updates to fix vulnerabilities and improve performance. These updates must be securely distributed and installed, with safeguards against rollback and tampering.
Availability and Resilience
Medical systems must remain operational even when under attack. This includes protection against denial-of-service attempts, hardware faults, and software crashes.
Industry Trends and Shifts
Shift-Left Security
Security is being addressed earlier in the development process. This includes the use of static code analysis and unit testing to identify issues before devices reach production.
Zero Trust of Connected Devices
The Zero Trust model limits access and assumes no device or user is trusted by default. Each interaction is authenticated and authorized, reducing the risk of internal threats.
Cloud-Native Security
As more devices connect to cloud platforms, security must be built into these systems. Cloud-native architectures use layered access controls, encrypted communication, and strong identity verification.
AI and ML for Threat Detection
Artificial intelligence is being used to monitor device behavior and detect unusual activity. These tools help identify security incidents quickly and improve response times.
Secure Hardware Design
Security features are now being built into hardware components, such as trusted execution environments and secure memory. This adds a layer of protection against physical attacks and firmware manipulation.
Regulatory & Standards Landscape
Medical devices are subject to strict regulatory requirements. These regulations guide how devices must be developed, tested, and managed:
- In the United States, HIPAA and FDA cybersecurity guidance are key.
- In Europe, GDPR and the Medical Device Regulation (MDR) apply.
- International standards such as ISO 13485,ISO 27001, ISO 27701, and IEC 62304 provide frameworks for security, privacy, and software development.
Medical & Connected Devices-Specific Regulations
The development and deployment of medical connected devices are governed by a combination of healthcare and cybersecurity regulations, varying across regions:
· United States:
o HIPAA ensures privacy of personal health information.
o The FDA’s cybersecurity guidance outlines premarket expectations for secure medical devices.
· European Union:
o GDPR enforces strict controls over data collection, processing, and storage.
o The Medical Device Regulation (MDR)mandates lifecycle risk management for connected medical systems.
· Global Standards:
o ISO 13485: Quality management systems for medical devices.
o ISO 27001 & ISO 27701: Information security and privacy information management.
o IEC 62304: Software lifecycle processes for medical device software.
These standards require comprehensive risk assessment, documentation, and system traceability.
Frameworks and Guidelines
In addition to formal regulations, several industry frameworks support best practices in security design:
· NIST connected devices Cybersecurity Framework
Helps identify, protect, detect, respond, and recover from cybersecurity threats in connected systems.
· UL 2900 Series
Certification standard addressing vulnerabilities, malware protection, and risk controls in connected products.
· IEC 80001
Focuses on managing risks associated with IT networks that include medical devices, especially in clinical environments.
These frameworks help ensure that devices are not only compliant but also built with layered, proactive security from design to deployment.
Current Developments in Vector Medical Engineering
Secure Toolchain for Development
Vector uses tools like PC-lint Plus and VectorCAST to improve code quality and traceability. Simulation environments allow developers to test software in realistic settings before devices are deployed.
SDMD Cloud Platform for Secure Deployment
The SDMD Cloud platform supports secure over-the-air updates, regulatory compliance, and real-time monitoring. Modules like Defender and Investigator offer additional protection and visibility into device behavior.
Future Directions and Challenges
As connected devices continue to expand, the healthcare sector must address several challenges:
- Many older devices lack modern security features.
- Devices from different manufacturers may not work together securely.
- post-quantum encryption is needed to protect against future computing threats.
- Edge computing introduces new risks that must be managed.
Conclusion
The security of connected medical devices is a growing concern and requires ongoing attention. Adopting secure development practices, complying with standards, and using modern technologies are all part of the solution. Vector Medical Engineering is addressing these challenges by incorporating security into its development processes and deploying secure platforms like SDMD Cloud.
Advancing Security in Medical Technology Together
Are you also affected by the upcoming Cybersecurity Resilience Act (CSRA), or struggling to get approval for your medical device without a proper security analysis? You are not alone – many companies across the industry are facing the same challenges.
At Vector, we are working closely with partners to navigate these new regulatory requirements and to develop effective solutions that ensure both compliance and patient safety.
If this resonates with you, we’d be happy to exchange ideas and support you on the way.